

In mid-June, the hacker collective known as Killnet made a bold announcement, claiming they were gearing up to “take down” the European banking system. They posted a video saying, “If Russia is under God's control, then who oversees Europe? That's right, the banking system. [...] No money, no weapons, no Kyiv regime! [...] You've never witnessed such challenges before. We are Killnet.” Despite several months passing, there has been no significant impact on the banking system, just as there was no impact on NATO, the USA, European governments, or Ukraine previously. Killnet had threatened them all with hacking, data breaches, and IT infrastructure disruption. While the group labeled itself the “Russian cyber army,” their achievements thus far resemble those of a regular army. As revealed by The Insider, this Kremlin media promoted group is composed of less-than-successful enthusiasts, and their limited successes were attributed to the efforts of GRU hackers.
Content
The rise of Killnet
Fighting foreign adversaries
Was there a botnet?
GRU handlers
Money from drug traffickers
Extortion or cooperation?
Reacting to shady sponsorship
Crisis of ideas
The rise of Killnet
In January 2022, a hacking group made a grand entrance with the statement, “Killnet is a brand-new network disruption technology.” This announcement marked the launch of their website and Telegram channel. In reality, Killnet is a service that offers illicit hacking services, including DDoS attacks starting at $5,000 per month. The existence of such services now allows individuals without IT expertise or a hacking background to carry out attacks on organizations that they find unfavorable. These clients could be business rivals or even representatives of government entities.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
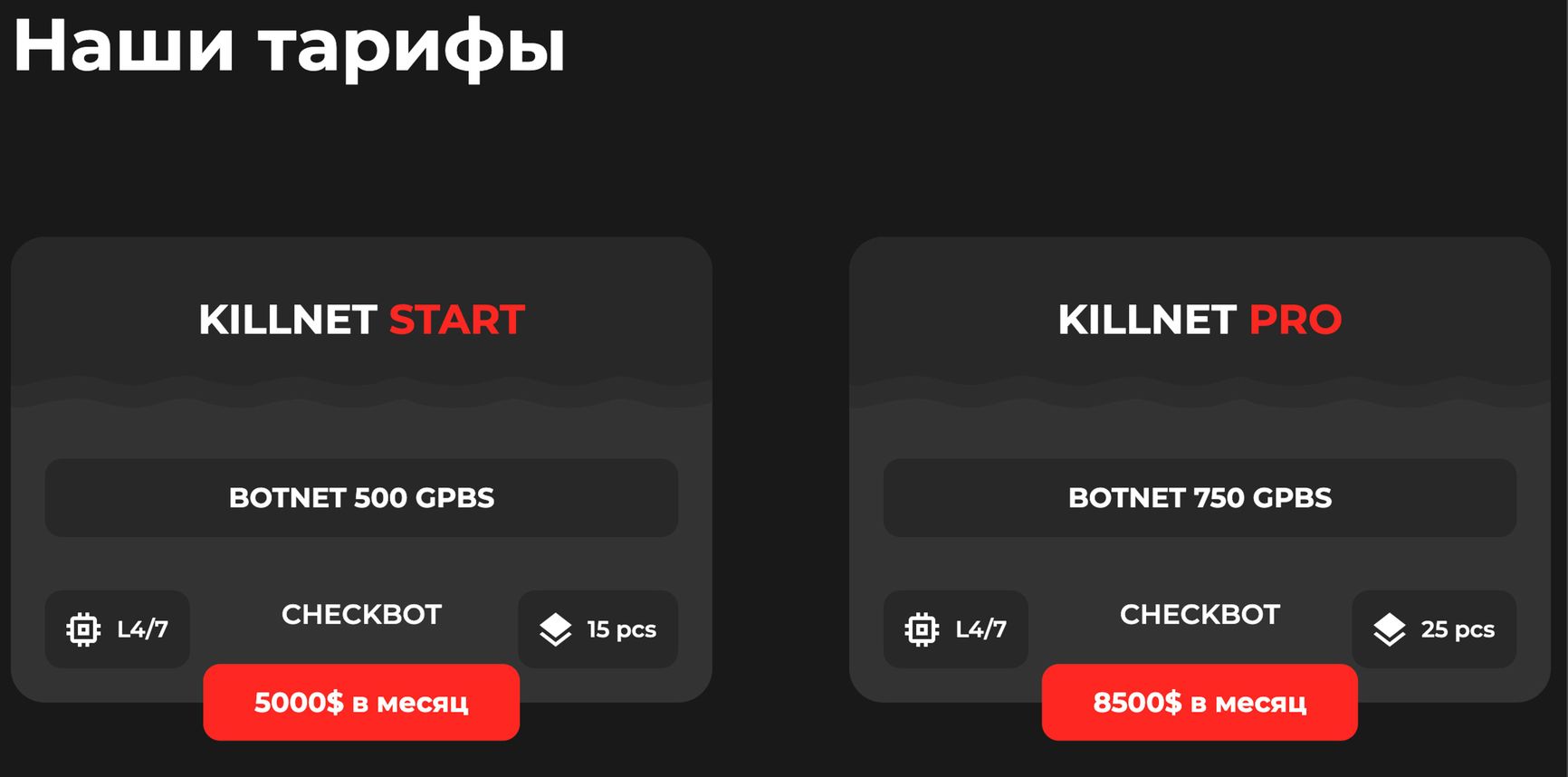
Screenshot of an archived copy of the Killnet website
The operators of Killnet assert that they control approximately 700,000 devices within their botnet network. In simpler terms, they have access to a vast number of compromised computers, routers, and other devices, extending to even internet-connected microwave ovens. These devices can be utilized to unleash a substantial flow of traffic towards a target's servers, causing their website or application to temporarily go offline. Essentially, Killnet has proclaimed itself as one of the largest botnets in history. To put it in perspective, the most renowned Mirai botnet had up to 900,000 infected devices at its peak.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
Killnet has proclaimed itself as one of the largest botnets in history
The Killnet service was promoted on specialized hacker forums by an individual using the alias KillMilk. He registered on the most popular darknet forum, Rutor, as early as October 2021. There, he opened a thread titled “DDoS Bros” and offered users his free services for website attacks. Prior to this, KillMilk was not well-known in the hacking community, according to The Insider's sources.
His messages on Rutor often had political undertones, which is generally discouraged in the hacker community. Even before Russia's full-scale invasion of Ukraine, he expressed negative views about Ukrainians. As a result, he was blocked in May 2022. The admin of Rutor explained the ban, saying, “KillMilk repeatedly drew unnecessary attention to the platform when he DDoS'ed government resources, then got involved in government-sponsored activities and left the forum.”
After Gulagu.net shared a video in November 2021 showing the torture of inmates in a hospital of the Federal Penitentiary Service in the Saratov region, KillMilk began sending threats to the Federal Penitentiary Service and promised to “take down” their websites. At the end of December of that year, Gulagu.net reported that hackers called Universal had contacted them, claiming to have “attacked all the Federal Penitentiary Service servers in Russia and declared vendetta against them.” Indeed, the Federal Penitentiary Service websites were inaccessible for several hours. The Telegram channel of Gulagu.net was filled with numerous links to the Universal group, and one commentator wrote, “KillMilk is awesome).” Just a couple of months later, on January 14, 2022, the Universal channel suddenly announced that they had “completed their support for human rights activists from Gulagu.net,” after which all their resources and accounts that shared links to their statements were deleted. Within a week of this, KillMilk announced the launch of the Killnet botnet on the Rutor forum. Forum users praised the service's excellent performance, and a well-known member under the alias “Dvuliky” (“Two-Faced”) wrote that it had already been “proven its effectiveness in dealing with the Federal Penitentiary Service.”
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
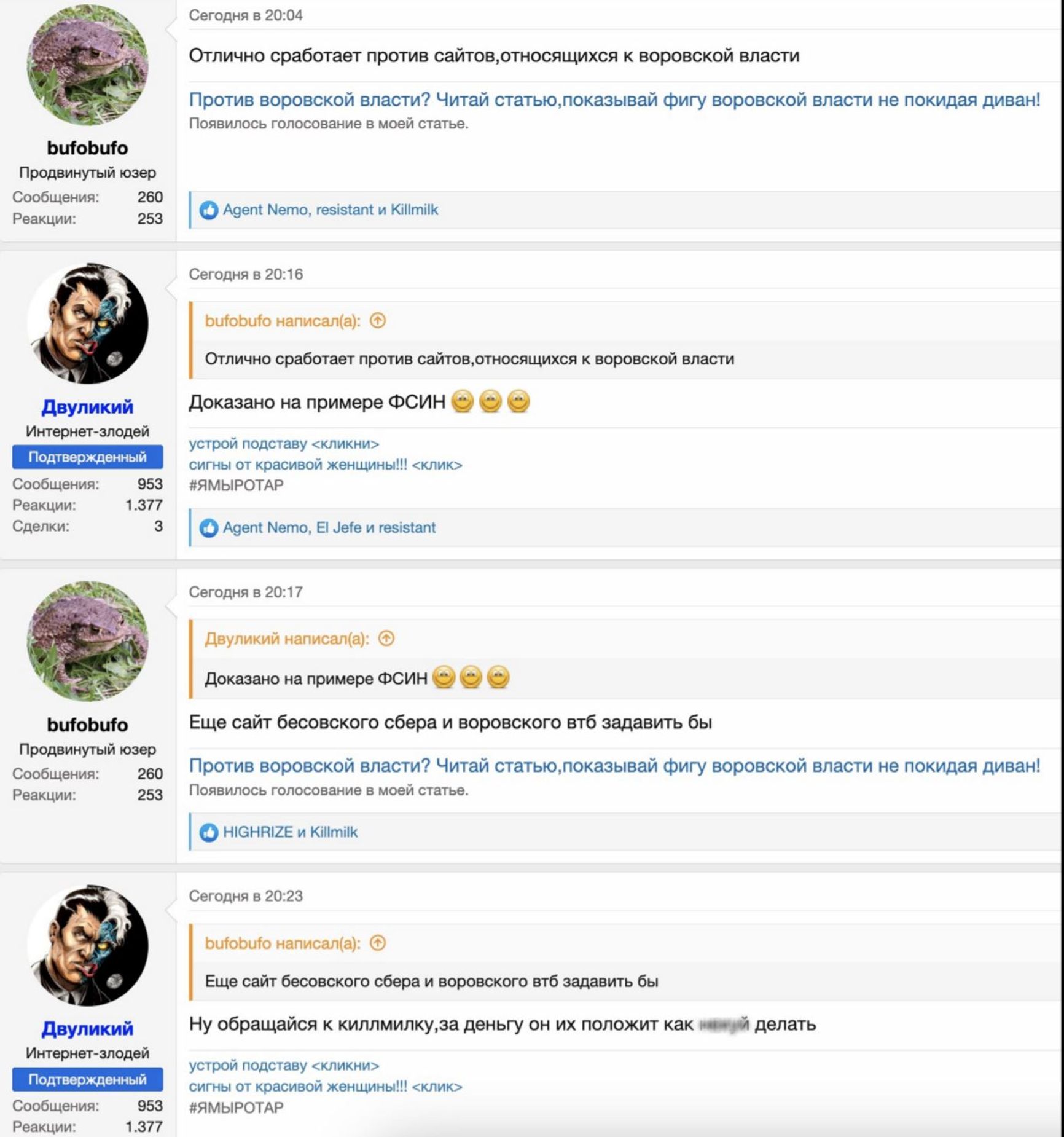
Screenshot from the Rutor forum, February 2022
KillMilk did not argue with this assumption and offered to be contacted for attacks on the Sberbank and VTB websites. A few days later, he came up with an even more ambitious idea - “to DDoS NATO.”
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
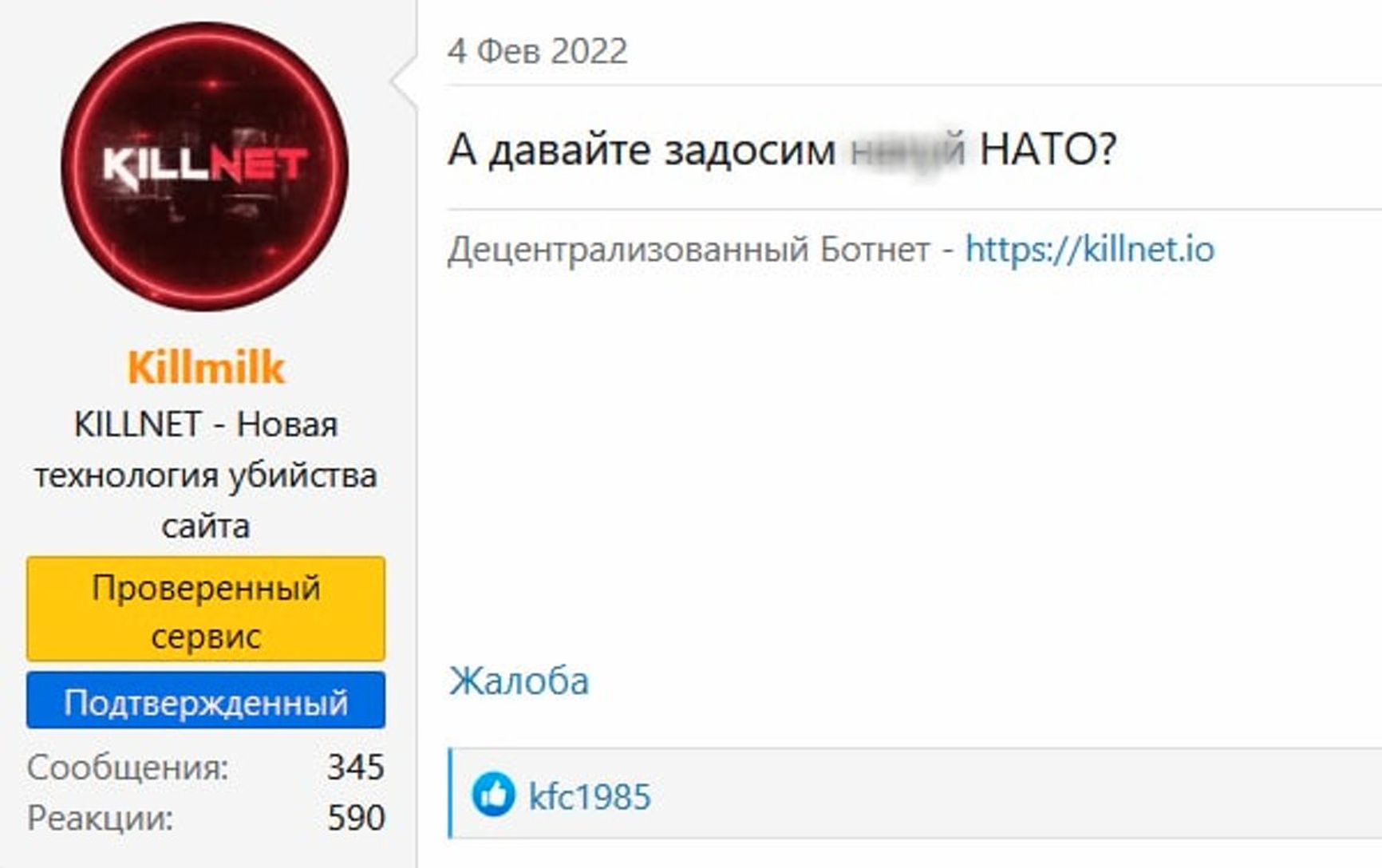
Screenshot from the Rutor forum, February 2022
However, KillMilk settled for a simpler target and on February 4th, he attacked the website of the blogger and former cybercriminal Sergey Pavlovich, as well as the cybersecurity news portal anonymoushackers.net, “to test the service.” The hacker was convinced that the website belonged to the international hacking group Anonymous, which in reality only has a Twitter account. It was on Twitter that they declared the start of a cyberwar against the Russian government after Russia invaded Ukraine. Killnet, on the other hand, announced a retaliatory war on the part of Russia, not forgetting to mention that they had already attacked a supposedly Anonymous-affiliated site. “We are not on good terms with our government, and we are cybercriminals... But when the threat is at our borders, [...] we stand up for defense in the best way we can,” explained a representative of Killnet to Darknet News.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
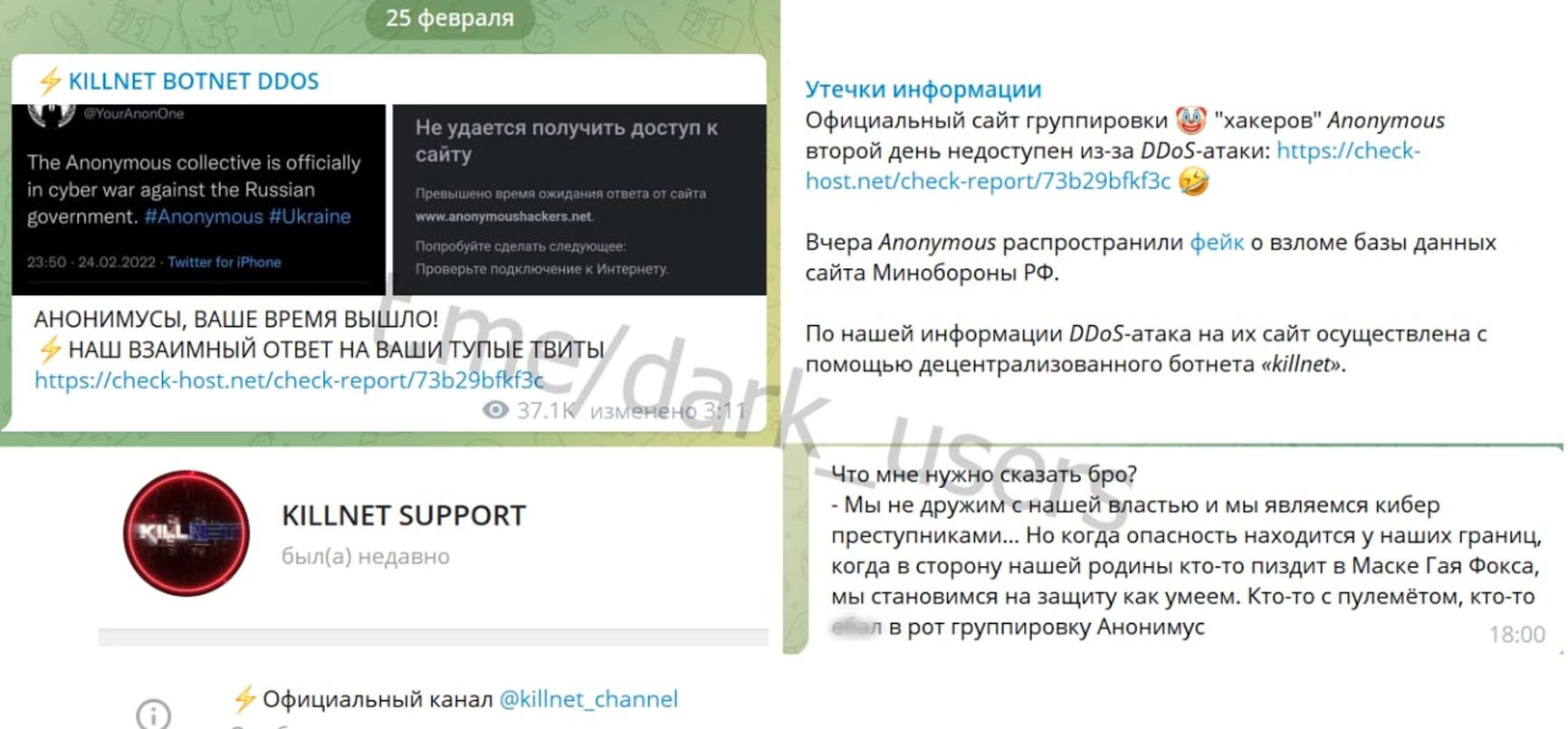
Screenshot from Darknet News
In the pursuit of more subscribers, Killnet continued to promote its “campaign” against Anonymous. This news gained attention from mainstream Russian media, ranging from Moscow 24 and RIA Novosti to Yevgeny Prigozhin's RIA FAN and Lenta.ru, as well as popular Telegram channels like “Kremlin's Washerwoman” and “War Correspondents of the Russian Spring.” Simultaneously, the network garnered followers among schoolchildren through viral TikTok videos.
Fighting foreign adversaries
Starting in March 2022, Killnet regularly posted information in their channels about DDoS attacks on Ukrainian, European, and American websites. The group claimed they attacked hundreds of sites. However, most of these were neither government websites nor directed against Russia in any way. Furthermore, the attacks were not substantial. As noted by the U.S. cybersecurity firm Mandiant, they had a minor impact and usually lasted for a short duration.
One of the first websites that Killnet targeted in their fight against foreign adversaries was polandhub.pl. “The attack on Poland's main media website POLANDHUB is a retaliation measure,” hackers wrote in their channel when Poland closed its airspace to Russian aircraft. It remains a mystery why a small portal about life in Poland in the Russian language, founded by Belarusian emigrants in 2020, became “Poland's main media site.” The attack lasted only a few hours, and it is unclear if anyone noticed it aside from the group itself.
This is not the only instance where Killnet mistook a small private website for a significant government target. The group claimed responsibility for a DDoS attack on Bradley International Airport's website in the United States in March 2022. Although this piqued the interest of U.S. law enforcement agencies because such activities are technically considered attacks on a country's critical information infrastructure, Killnet's actions had no impact on the airport's operations.
In June 2022, the group announced a new “high-profile target” - the U.S. Electronic Federal Tax Payment System. However, the attack targeted the portal of a company that assists Americans in preparing their tax returns. In July, Killnet claimed to have blocked the U.S. Congress website - though it turned out to be just the website of the Library of Congress, which was unavailable for only two hours.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
In June 2022, Killnet announced a new “high-profile target” — the U.S. Electronic Federal Tax Payment System
In August, KillMilk declared war on the Lockheed Martin corporation, which manufactures artillery rocket systems such as HIMARS. Threats against the corporation appeared in the group's channels for two weeks; however, their websites continued to function. Eventually, the group claimed to have stolen Lockheed Martin's data. As proof, they published a video allegedly containing a list of the corporation's employees, along with their phone numbers and email addresses.
“It does appear that they are or were genuine Lockheed employees, however that does not necessarily confirm that the company was breached. For example, this could be a re-hash of old or opensource data in an attempt to undermine the organization and intimidate its employees,” commented Louise Ferret, an analyst at Searchlight Security, on Killnet's posts. Afterward, there was no further mention of the “breach” of Lockheed Martin. Similarly, no information emerged about leaks from the U.S. Internal Revenue Service, data of 10,000 FBI employees, and many other breaches that Killnet had loudly announced on their channels.
One of Killnet's biggest promises was made in June 2023. To “create a banking panic in the European chicken coop,” they pledged to paralyze the banking system. In doing so, they cited various terms like IBAN (International Bank Account Number), SEPA (Single Euro Payments Area), WISE (a British company specializing in cross-border transfers), SWIFT (the international interbank messaging system), and WIRE (the exact meaning the hackers had in mind is unknown, but in English, any non-cash payment is referred to as a wire transfer). Despite the loud threats that quickly spread through Russian media, nothing happened with the European banking system, transfer systems, or IBAN standards in the following months.
Most cybersecurity companies specializing in investigating Killnet's activities believe the group is primarily engaged in self-promotion. “Regular announcements of creating, and cooperating with, new groups are at least partly an attempt to attract the attention of Western media and exaggerate the impact of their own operations,” Mandiant notes in its report.
“Do not take any of Killnet's claims at face value given that the collective’s regular creation and absorption of new groups is at least partially an attempt to continue to garner attention from Western media and to enhance the influence component of its operations, both in the public sphere and among cybercriminals,” states the U.S. Healthcare Cybersecurity Center in its bulletin. “The impact of [Killnet's] operations on national security is relatively limited. This assessment is purely based on pro-Russian hacker groups’ earlier and current behavior and their limited resources,” the analytical company Grey Dynamics reports.
Nevertheless, cybersecurity agencies from Australia, Canada, New Zealand, the United Kingdom, and the United States jointly included Killnet in a list of threats due to the war between Russia and Ukraine, alongside hacking groups long associated with the GRU.
Pavel Sitnikov, the head of the cybersecurity company XPanamas, believes that despite the modest results, and sometimes the complete absence thereof, KillNet's actions cannot be considered entirely unsuccessful:
“As DDoS attacks, [Killnet's attacks] are 100% successful, but only in the moment - that's the nature of DDoS. This type of attack is very easy to execute and therefore involves more people with fewer abilities.”
Was there a botnet?
The political engagement of the Killnet group sparked disapproval within the hacker community. As mentioned earlier, most forums do not welcome or even prohibit discussions about politics. However, Russia's invasion of Ukraine brought about some changes. Before February 2022, Russian, Ukrainian, and Belarusian hackers were somewhat united in their own community. They collaborated, exchanged data “leaks,” or purchased them from each other. However, after the war began, the community split into those supporting Russia and those supporting Ukraine. In both camps, “hacktivism” flourished, including website and database breaches, doxxing of military personnel and activists, DDoS attacks, and disinformation campaigns.
For instance, the ransomware group Conti, one of the most well-known and profitable groups specializing in ransomware attacks, announced its support for the Russian authorities. In response, Ukrainian members of the group leaked their correspondence from the entire previous year. Some other cybercriminals also supported the Russian side, but most of them remained neutral. After its high-profile information campaign claiming victory over Anonymous, Killnet adopted a clear pro-Russian stance. The newly minted fighter against the West was promptly promoted on propaganda resources where KillMilk openly declared his intentions:
“In Russia, I will become a hero, and abroad – a criminal. Soon, KillNet and I will launch powerful attacks on European and American companies, indirectly leading to casualties. I will exert every effort to make these regions and countries answer for the death of each of our soldiers.”
However, contrary to the successful PR campaign, reports began to surface suggesting that Killnet was conducting attacks using someone else's botnet and didn't have its own botnet at all. For example, the attack on a website allegedly affiliated with Anonymous was carried out by the owner of the IP stresser Chemistry (a service for testing the network or server for stability). He disclosed this on his channel at the very beginning of Killnet's PR campaign. The IP stresser's owner shared screenshots of the correspondence in which Killnet asked him to “take down” websites of the Right Sector, UNA-UNSO, and other Ukrainian nationalist organizations. After the correspondence was shared online, the Killnet account blocked him.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
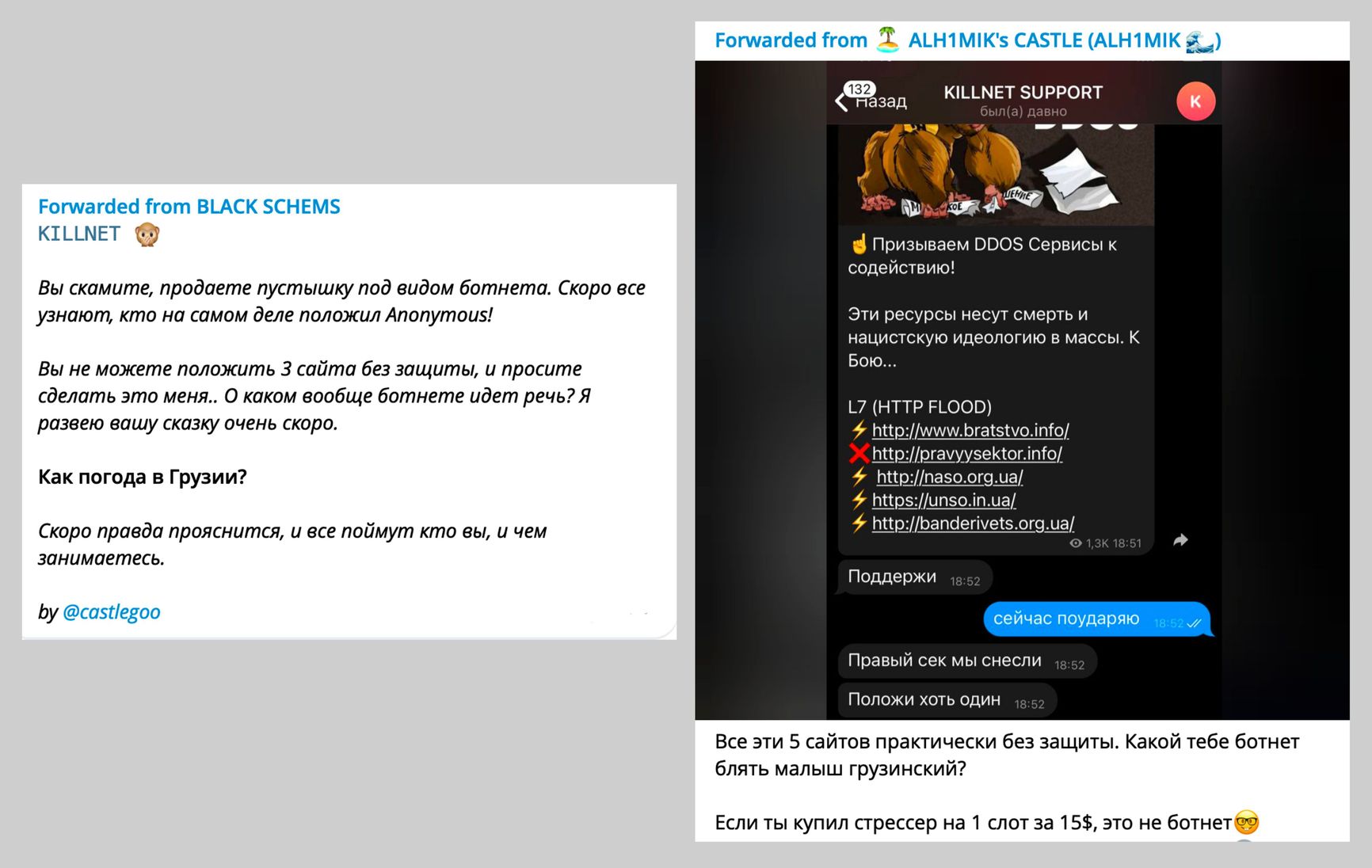
Screenshots from the Chemistry IP stresser's channel
Two veteran members of darknet hacker forums informed The Insider about Killnet's involvement in reselling rented botnet and IP stresser services. Another Rutor forum member claimed in May 2022 that Killnet was reselling services from stresser.us, and a few months later, the group openly advertised this service.
Besides, there were links to third-party services even on Killnet's own channel. For instance, Killnet proudly announced that the owner of stresser.tech had taken down one of the websites of Ukrainian nationalists. And Anonymous Russia, a group affiliated with Killnet, didn't hide the fact that they conducted attacks through stressID.
During its eighteen months of existence, Killnet repeatedly promoted various stressers and botnets, referring to them as partners, such as the Passion Botnet and Tesla Botnet. The group no longer publicly offered its own DDoS services after the start of its political activities. Perhaps this protected someone from unsafe collaboration: Killnet promised complete anonymity to its clients, but after the group's website was hacked (back in the spring of 2022), it was revealed that the administrators stored unencrypted passwords and other data of their registered clients.
GRU handlers
One of the veterans on Rutor, in a conversation with The Insider, speculated that with such limited technical expertise (no proprietary resources, brief attacks, and easy targets), Killnet managed to achieve PR success through connections with certain state handlers who linked them to the XakNet group. XakNet emerged seemingly out of nowhere shortly after the start of Russia's war in Ukraine.
The XakNet Team channel appeared on Telegram on March 1, 2022, and immediately reported a successful DDoS attack on the website of the Ukrainian president. The next day, the group hacked all regional and other government websites in Ukraine. At that time, DDoS confrontation between activists from both countries had been ongoing for several days.
XakNet Team used the logo of the old Russian-language hacker forum with the same name. Members of this community had already engaged in state-sponsored hacking. During the 2008 war in Georgia, some of them targeted Georgian government websites. At least one defacement by this group made it into a CNN report.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data

Screenshot from the CNN report, August 2008
While there were speculations in the media that the Kremlin was behind the attacks, the defacements and DDoS attacks seemed to be carried out by volunteers. The forum has been closed for many years, and its participants are likely retired, according to a well-known user from the Rutor forum, as reported by The Insider.
On the other hand, a member of the new XakNet group revealed themselves quite early on, discussing the attacks and mocking Anonymous:
“All that the kids in masks could demonstrate was organizing a DDoS attack. And they even messed that up. After pairing up, ForceFull DDoS and Killnet gave a much more powerful response, completely taking down all government websites in Ukraine. Even in this aspect, where the whole world acknowledged the absolute leadership of Anonymous, two guys from Russia trampled them and showed how to do it correctly, Russian style.”
If Killnet did not have its own DDoS capabilities, the same cannot be said for the other mentioned participant in the XakNet attacks. ForceFull DDoS is identified as a member of the team in XakNet chats. They had been advertising website attack services since at least 2014 and continued to post commercial advertisements until the spring of 2023.
However, their claim to “completely take down all government websites in Ukraine” only lasted for a few hours. Subsequently, the administrators of government websites simply restricted access to portals in the gov.ua domain from anywhere outside Ukraine. This method of protection against DDoS attacks is employed because traffic typically originates from outside the country.
Interestingly, the XakNet channel, where the report of the attack on Ukrainian websites surfaced, was created on March 1, but the attacks began on February 23, just a few hours before the start of military actions. This was confirmed by Ukraine's Minister of Digital Transformation, Mikhail Fedorov, and later by KillMilk in an interview with Lenta.ru. “We delivered our first blow to the gov.ua domain, [...] about 67 resources stopped working. [...] This happened ten hours before the start of the special operation, and we didn't publicize this action,” he said, without explaining the motive behind attacking Ukrainian government websites.
However, XakNet's notoriety in patriotic channels—and subsequently, its audience—grew not because of this DDoS attack. A week after the start of the war with Ukraine, XakNet published files on their channel, supposedly containing personal data of Ukrainian military personnel. The group later claimed responsibility for several hacks and shared data allegedly stolen from Ukrainian government ministries and law enforcement agencies.
It's worth noting that the hacks of Ukrainian websites for which XakNet claimed responsibility were likely carried out by someone else. In mid-January 2022, several Ukrainian government portals were subjected to cyberattacks. Computers were infected with the WhisperGate virus, which posed as ransomware but, in reality, gained access to data on the servers of Ukrainian government sites and NGOs, and wiped the data. The attack was investigated by Microsoft, which concluded that it was the work of the GRU. Immediately after the attacks, fragments of data stolen from Ukrainian government servers were published on RaidForums and on the Free Civilian website in the darknet. The archives that appeared on the XakNet channel after Russia's full-scale invasion of Ukraine belonged to the same agencies and partially matched those advertised for sale on Free Civilian resources in the darknet and on Telegram.
Mandiant, an American company specializing in cybersecurity, believes that XakNet coordinates its attacks with, or is directly linked to, GRU hackers (click here to read more about the GRU hacker attack on Ukraine).
Money from drug traffickers
Although Killnet was initially promoted as a commercial service, by April 2022, they officially stated that they had stopped providing paid services. Links to bank cards and wallets for donations were posted in the Killnet and KillMilk channels, and the group's founder claimed that the attacks by his group were sponsored by “enthusiasts and patriots of their country” who had “no connection to the authorities.” Furthermore, in September, KillMilk complained that he had to take out five loans for “resisting enemies” (spelling preserved):
“At the moment, I have no opportunity to continue my activities. At the moment, my destructive activity boils down to one thing - no finances, no servers, but I have more than 5 loans that I took out to support the Killnet team! It's embarrassing even to write such a thing, but it's even more embarrassing for those people who have great opportunities but don't want to help us move in one direction without failures - towards Victory!”
The Insider discovered that money began to flow into the first Bitcoin wallet that Killnet set aside for donations even before the war. From February to April 2022, it received nearly 0.87 bitcoins (approximately $23,800). Most often, the amounts came in instalments of several hundred dollars each, with the largest being around $6,000. In addition to this, Killnet could have earned money from advertising hacker services.
However, one of their main sources of income was most likely their connection to the drug marketplace Solaris. KillMilk spoke about their friendship with this platform in an interview with the propaganda outlet Russia Today. “Thanks to their attention to us, Killnet continues to operate at full capacity,” he said in an interview in October. “Help came from where we least expected it! The government of the black market SOLARIS supports Killnet's activities and provides us with a solid foundation to continue our fight and develop the KILLNET team!” he added in his channel (the post was then deleted). A few months after the interview, Solaris confirmed the collaboration on its forum. Investigative company TRM Labs discovered at least one transfer of $50,000 from Solaris wallets to Killnet wallets.
So, where did the trading platform Solaris come from, and why did it help Killnet? In early April 2022, German authorities announced the liquidation of the largest online drug market, Hydra. Before its closure, there were about 19,000 stores selling illegal goods on it. Customers were lured to various platforms after it closed, including Rutor, which was the second largest at that time. While Rutor had primarily been used for selling fake documents, weapons, and illegal services before, it now began attracting drug shops. Simultaneously, the relatively unknown marketplace Solaris joined the market redistribution, along with Kraken, OMG, and other platforms. Some of them were created and moderated by former Hydra employees. A struggle for control of the market emerged among these platforms.
Rutor was likely sold in May 2022 (this was reported in the closed sections of the forum by its administrators WD, John, and Maskarad). Starting from June, Rutor began experiencing regular DDoS attacks. Darknet media outlets cited multiple confirmations that the attacks on Rutor were conducted by the new platforms - Solaris and Kraken. On June 20, a threat to destroy Rutor appeared in the Killnet channel, along with a hint that the forum had been bought by the Security Service of Ukraine (SBU). These messages were deleted a few minutes later.
On August 1, 2022, Rutor was hacked, and a few days later, KillMilk promised an “exclusive Rutor leak” in his channel. However, as often happened with Killnet, the threats turned out to be empty, and no leak occurred. KillMilk subsequently deleted the posts. But by August 15, Killnet declared war on Rutor and called for a DDoS attack on it (spelling preserved):
“Rutor is a unit formed by the SBU. I don't know how the profiteers manage to survive there, zero trust in it, f*ck it... I officially declare the start of the dismantling of the Ukrainian Rutor forum. [...] I call on all supporting hack groups and communities to join the DDoS attacks on the profiteer forum Rutor.”
Despite the attacks, Rutor continued to function smoothly. Instead, “hacktivists” attracted new customers to the Solaris platform. One of its moderators mentioned at the time when Killnet announced a DDoS attack on Rutor, “If Killnet fulfills its promise, a stream of people will rush in.” However, it's unclear exactly what kind of promise Killnet made.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data

Screenshot from the Solaris forum (source: ZeroFox Intelligence)
Killent also declared war on another competitor, BlackSprut. They accused BlackSprut of having connections with Ukraine. The group claimed to have hacked the platform and was ready to sell data about stores, customers, and drugs planted in urban areas (so-called “drop points”) for $250,000. However, these threats were likely a bluff, as BlackSprut continued to operate.
Extortion or cooperation?
In addition, a Solaris moderator wrote that Killnet managed to obtain a million rubles through extortion from Rutor's handler.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
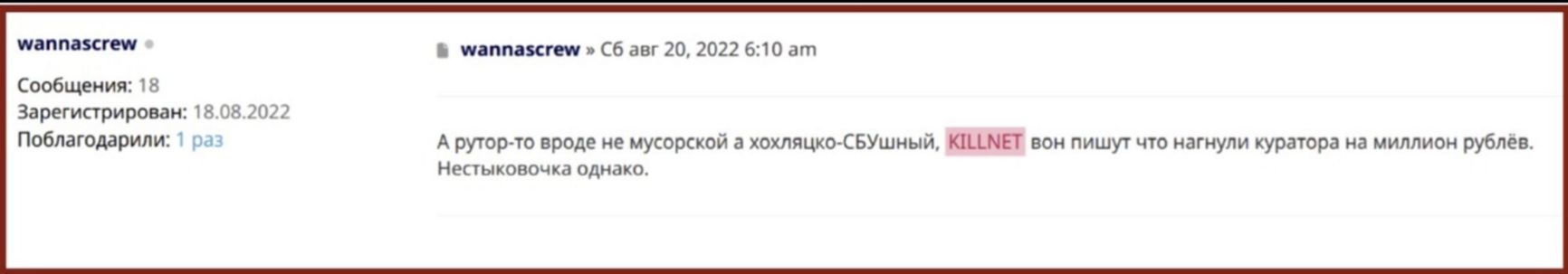
Screenshot from the Solaris forum (source: ZeroFox Intelligence)
Killnet themselves reported receiving money from Rutor, bragging about their successful scam. According to the group, the drug marketplace allegedly gave them money to stop attacking them, but they had no intention of doing so. They promised to transfer part of the funds to orphanages in Russia and provide evidence of doing so. However, no evidence ever surfaced – just like in other instances where the group promised charitable donations.
Meanwhile, one of the administrators of the Rutor platform admitted to attempting to purchase advertising on Killnet channels. Therefore, it's possible that Rutor didn't transfer the money to get the group to stop DDoSing their servers. KillMilk had requested $10,000 for 20 days of regular advertising on four of his channels. The hacker cited media publications about his group as examples, adding that publications themselves were happy to take news from the Killnet channel. He also boasted that information about the group made it to Yandex Top.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
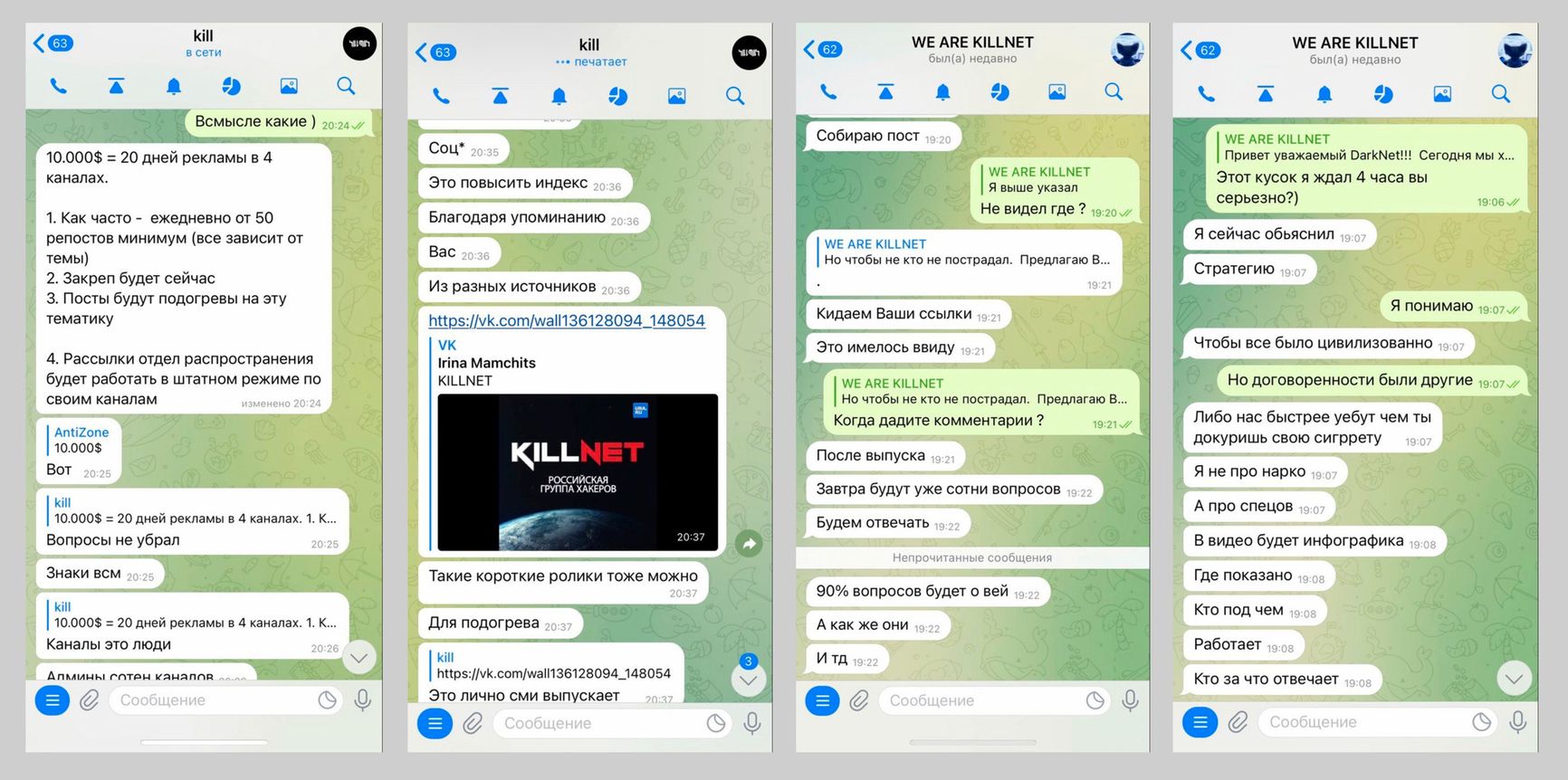
Screenshots of correspondence between KillMilk and a representative of Rutor about ad sales
In the end, a paid Rutor post appeared on the Killnet channel on August 19, but the customer was dissatisfied. The post was deleted, and KillMilk promised that “the new owner of the drug forum Rutor will be liquidated soon.” A year has passed since then, but the forum continues to operate.
Reacting to shady sponsorship
The news of sponsorship from the Solaris marketplace (which controlled about a quarter of the Russian drug market) did not sit well with all of Killnet's supporters. Requests to comment on this questionable collaboration began appearing in the group's chats. However, moderators were deleting such questions and banning those who asked them.
KillMilk's statement also caught the attention of Killnet's opponents. To study how Solaris operated, U.S. cybersecurity specialist Alex Holden infiltrated the platform in the summer of 2022. When KillMilk admitted that his activities were sponsored by a drug forum, Holden conducted an unusual campaign. He transferred 1.6 bitcoins (approximately $25,000) from the Solaris marketplace wallet to the Zhiznelyub fund in Kyiv, Ukraine, and then shared information about it and leaked the entire infrastructure of the forum, its security systems, internal and external correspondence of its participants. “If KillMilk says that Solaris is a significant support, why not remove this support?” Holden commented.
Less than a month after Holden leaked Solaris data, the drug platform was taken over by its competitor, Kraken. None of Killnet's channels reacted to this news in any way. However, when other moderators relaunched Solaris in February, KillMilk immediately congratulated them on their return. However, he quickly deleted this post. This was because, at that time, Killnet's official stance had drastically changed: they had embarked on a path to combat drug dealers.
Nevertheless, it's unlikely that KillMilk's friendship with the drug shop will be easily forgotten: “Milk has been given a death sentence by Russian dealers,” a hacker from another pro-Russian group reacted to an attempt to dox him. “I wouldn't want to see the real doxxing of Milk, no matter how much I dislike him. This person is an irresponsible d*ckwad, and because of him, his relatives, loved ones, and friends will most likely suffer.”
Crisis of ideas
Despite assurances that Killnet had become a purely non-commercial patriotic organization since the beginning of the war, its members constantly attempted to profit from the audience and brand they had built. In March 2023, KillMilk announced the launch of the private military hacker company (PMHC) Black Skills and invited investors. He asked for a 51% stake in the company in exchange for 5 million rubles. Or maybe dollars, it's unclear which currency. KillMilk cited the need for finances as the reason for this decision.
“Killnet's altruism and hacktivism have come to an end. [...] We continue our destructive activities in the name of our homeland! We cannot survive on donations and promised support from sponsors. We also defend the interests of the Russian Federation but now we also take orders from private and government individuals!”
Apparently, no private or government individuals were interested in such an offer. After two months of constant advertising for PMHC, Killnet's leader stated that he would not create cyber counterparts to the Wagner PMC and continued to solicit donations.
KillMilk was clearly enamored with the sponsor of the Wagner PMC, Yevgeny Prigozhin. He congratulated him on his birthday in his channel, regularly reposted his statements, and on June 24, during the Wagner uprising, he stated that he had gone “with the Wagners to solve the issue in Moscow,” but the “tour ended earlier.” After Prigozhin's death was confirmed in August, all channels associated with Killnet changed their avatars to the Wagner PMC logo.
In parallel with the PMHC idea, Killnet attempted another monetization effort and announced the launch of the “Dark School.” The cost of education was $500, and they were planning to teach “professional cyber warfare” - for example, DDoS, creating and promoting fake content, doxxing. In the end, students were only sent outdated materials every few weeks, openly available on the internet. For example, a book from 2007 in an entertaining manner explaining what social engineering is. According to information from the Telegram channel Dark Femida, some students tried to get their money back for the training because after a few weeks, they stopped receiving materials. However, KillMilk never returned the money.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data
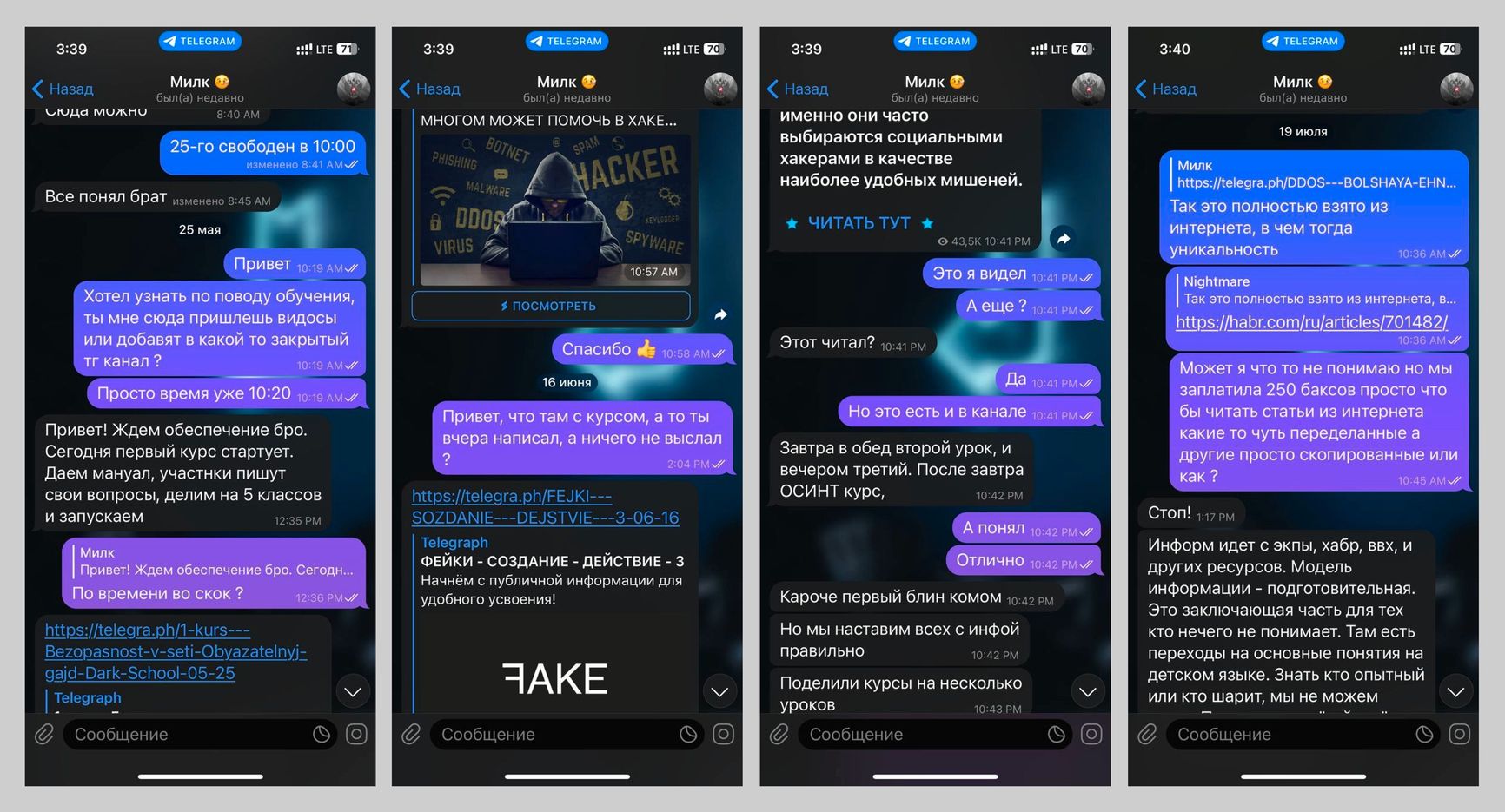
Screenshots from the Telegram channel Dark Femida
In addition, Killnet launched its own cryptocurrency exchange, a “lookup” bot based on someone else's data, its own dark web media outlet, continued to promote its DDoS services, and attempted to launch its dark web forum - similar to Rutor's. However, the forum was immediately taken down by adversaries, and Killnet failed to sell ads on it. Just like in regular business, working in the dark web relies on trust. However, trust within the Killnet team was constantly questioned. On one hand, the group's founder constantly searched for traitors and “intriguers” within the team. Some “old-timers” were kicked out of the group, while others left due to burnout or disagreement with the goals - for example, when Killnet called for attacks on European medical institutions' websites.
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data

Screenshot from the KillMilk channel
The revelation about the identity of Raty, the leader of the Anonymous Russia group, caused shock within the Killnet community. Anonymous Russia was not related to the international Anonymous group and essentially engaged in similar DDoS attacks as Killnet. It was headed by a hacker using the pseudonym Raty. In April 2023, it was discovered that Raty was actually Arseniy Yeliseev, an 18-year-old Belarusian from Gomel. In his home country, he was arrested - according to the Ministry of Internal Affairs, while still a minor, Yeliseev attempted to steal an antenna belonging to a local telecommunications operator. Following the news of his arrest, KillMilk promptly leaked Yeliseev's identity. He also claimed that Yeliseev had caused trouble for a local law enforcement officer due to jealousy, which led to his arrest. Whether the authorities knew at the time of his arrest that Yeliseev was connected to a hacking group is unknown, which is why some members of Killnet criticized KillMilk's actions, resulting in bans. One source of outrage was the publication of Yeliseev's passport, as verification of identity through documents was required to join KillMilk's ranks.
After the scandal, KillMilk promised to dox the law enforcement officer responsible for Yeliseev's arrest but never followed through. He also declared war on Belarus but later deleted all related messages. As a result, Yeliseev faced charges in Belarus for illegal actions regarding information (Article 203-1, parts 1 and 2 of the Belarusian Criminal Code) and the dissemination of knowingly false information about danger (Article 340, part 1 of the Belarusian Criminal Code). On September 1st, he appeared before the court.
Written in association with Alexey Remizov
A botnet, i.e. a network of devices infected with a virus of the same name, which enabled the organization of major DDoS attacks in 2016-2017.
Sharing of personal data